Broadcom Technical Interview Questions, Broadcom Interview Questions for Experienced
1 / 8
No Discussion on this question yet!
No Tags on this question yet!
2 / 8
No Discussion on this question yet!
No Tags on this question yet!
3 / 8
No Discussion on this question yet!
No Tags on this question yet!
4 / 8
No Discussion on this question yet!
No Tags on this question yet!
5 / 8
No Discussion on this question yet!
No Tags on this question yet!
6 / 8
1) Sort the array in ascending order.
2) Initialize two index variables to find the 'S'
  elements in the sorted array.
    (a) Initialize first to the leftmost index: l = 0
    (b) Initialize second the rightmost index: r = ar_size-1
3) Loop while l < r.
    (a) If (A[l] A[r] == S) then return 1
    (b) Else if( A[l] A[r] < sum ) then l
    (c) Else r--  Â
4) No 'S' in whole array - return 0
No Tags on this question yet!
7 / 8
No Discussion on this question yet!
No Tags on this question yet!
8 / 8
No Discussion on this question yet!
No Tags on this question yet!
1 / 13
No Discussion on this question yet!
No Tags on this question yet!
2 / 13
No Discussion on this question yet!
No Tags on this question yet!
3 / 13
No Discussion on this question yet!
No Tags on this question yet!
4 / 13
No Discussion on this question yet!
No Tags on this question yet!
5 / 13
A processor will have processing word length as that of data bus size. On a 32 bit machine, the processing word size will be 4 bytes.
Data structure alignment is the way data is arranged and accessed in computer memory. It consists of two separate but related issues: data alignment and data structure padding.
No Tags on this question yet!
6 / 13
struct xx {
char a;
int b;
};
printf("%d", sizeof(struct xx));
8 in case of union it will be 4Â
No Tags on this question yet!
7 / 13
No Discussion on this question yet!
No Tags on this question yet!
8 / 13
No Discussion on this question yet!
No Tags on this question yet!
9 / 13
There's one input message queue where can we read from, and there is three output message queue that you can write to. The message has alphanumeric key value. There could be duplicate key values coming out of the input queue and once we put a key value say "ABC1234" to output queue-1, whenever we get a key value ABC1234 it should go to queue-1 only. Also, we should try to balance the load among the 3 output queues.
No Discussion on this question yet!
No Tags on this question yet!
10 / 13
No Discussion on this question yet!
No Tags on this question yet!
11 / 13
No Discussion on this question yet!
No Tags on this question yet!
12 / 13
(a) When both are on same network.
(b) When both are on different networks.
Explain which layer takes routing decision and how.
[Host-A]-----------------------------[Host-B]
When both are on the same network (Scenario: a)
Host-A:192.168.2.2
Subnet mask of Host-A: 255.255.255.0
Host-B: 192.168.2.100
When both are on different networks: (Scenario: b)
Host-A: 192.168.2.2
Subnet mask of Host-A: 255.255.255.0
Host-B: 192.168.1.100
Subnet mask of destination IP is not required. Consider both the scenarios, Now if Host-A tries to send some packets to Host-B it is obvious to identify the immediate hop where host-A should forward the packets.This is achieved by below manipulation
1. Perform bitwise AND operation between Host A IP and subnet mask of the source and let the result be subnet address 'x' ( In scenario (a) if we do that we get x =192 .168.2.0 and similarly for scenario (b) x= 192.168.2.0)
2. Perform bitwise AND operation between Host B IP and subnet mask of the source and let the result be subnet address 'y' (In scenario (a) if we do that we get y= 192.168.2.0 and similarly for scenario (b) y= 192.168.1.0)
Observe that for the scenario (a) both x and y are the same so that Host A understands that destination is in the same subnet and now it sends an ARP broadcast to get MAC details and sends the packets directly to the destination host.
Now let's consider scenario (b) where x and y are different. So it is vivid that destination host is not in direct reach and hence source host forwards the packet to default gateway router .now the default gateway router acts as the source and the same manipulation is done here. The destination address remains unchanged in the routing process.
No Tags on this question yet!
13 / 13
Input: 10 01 11 00 Output: 01 10 11 00
#include
unsigned int swapBitsInPair(unsigned int x)
{
/*
extracts the high bit position and shifts it to the low bit position.
similarly extracts the low bit from each pair and shifts it to the high bit position.
The two parts are then combined using bitwise OR
*/
return ((x & 0b10101010) >> 1) | ((x & 0b01010101) << 1);
}
int main()
{
unsigned int x = 156;
printf("%d", swapBitsInPair(x));
return 0;
}
No Tags on this question yet!
1 / 14
No Discussion on this question yet!
No Tags on this question yet!
2 / 14
Priority-based flow control (PFC), IEEE standard 802.1Qbb, is a link-level flow control mechanism. The flow control mechanism is similar to that used by IEEE 802.3x Ethernet PAUSE, but it operates on individual priorities. Instead of pausing all traffic on a link, PFC allows you to selectively pause traffic according to its class.
Standard Ethernet does not guarantee that a packet injected into the network will arrive at its intended destination. Reliability is provided by upper-layer protocols. Generally, a network path consists of multiple hops between the source and destination. A problem arises when transmitters send packets faster than receivers can accept them. When receivers run out of available buffer space to hold incoming flows, they silently drop additional incoming packets. This problem is generally resolved by upper-layer protocols that detect the drops and request re-transmission.
Applications that require reliability in Layer 2 must have the flow control that includes feedback from a receiver to a sender regarding buffer availability. Using IEEE 802.3x Ethernet PAUSE control frames, a receiver can generate a MAC control frame and send a PAUSE request to a sender when a specified threshold of receiver buffer has been filled to prevent buffer overflow. Upon receiving a PAUSE request, the sender stops transmission of any new packets until the receiver notifies the sender that it has sufficient buffer space to accept them again. The disadvantage of using Ethernet PAUSE is that it operates on the entire link, which might be carrying multiple traffic flows. Some traffic flows do not need flow control in Layer 2, because they are carrying applications that rely on upper-layer protocols for reliability. PFC enables you to configure Layer 2 flow control selectively for the traffic that requires it, such as Fibre Channel over Ethernet (FCoE) traffic, without impacting other traffic on the link.
No Tags on this question yet!
3 / 14
64-byte MAC control frame is used by both IEEE 802.3x PAUSE and PFC. In both cases, numeric values can be used to describe the requested duration of PAUSE. However, since PFC acts independently on eight different CoSs, the frame describes the PAUSE duration for each CoS.
The PAUSE duration for each CoS is a 2-byte value that expresses time as a number of quanta, where each represents the time needed to transmit 512 bits at the current network speed. A PAUSE duration of zero quanta has the special meaning of unpausing a CoS. Typical implementations will not try to guess a specific duration for PAUSE, instead relying on the X-ON and X-OFF style behavior that can be obtained by setting PAUSE for a large number of quanta and then explicitly resuming traffic when appropriate.
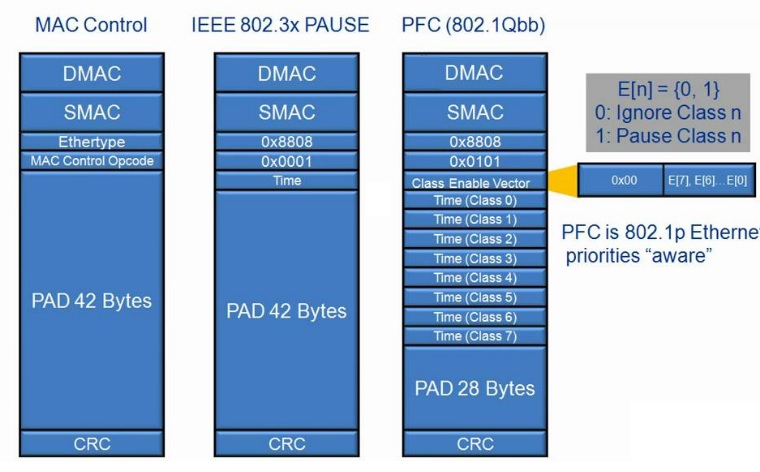
No Tags on this question yet!
4 / 14
No Discussion on this question yet!
No Tags on this question yet!
5 / 14
No Discussion on this question yet!
No Tags on this question yet!
6 / 14
No Discussion on this question yet!
No Tags on this question yet!
7 / 14
Condition: No extra memory is to be used.
No Discussion on this question yet!
No Tags on this question yet!
8 / 14
No Discussion on this question yet!
No Tags on this question yet!
9 / 14
No Discussion on this question yet!
No Tags on this question yet!
10 / 14
The memcpy function is used to copy a block of data from a source address to a destination address. The prototype for memcpy is
void * memcpy(void * destination, const void * source, size_t num);
#include
#include
void myMemCpy(void *dest, void *src, size_t n)
{
// Typecast src and dest addresses to (char *)
char *csrc = (char *)src;
char *cdest = (char *)dest;
// Copy contents of src[] to dest[]
for (int i=0; i
}
int main()
{
char csrc[] = "broadcom interview";
char cdest[100];
myMemCpy(cdest, csrc, strlen(csrc)+1);
printf("Copied string is %s", cdest);
return 0;
}
No Tags on this question yet!
11 / 14
#include
#include
int main()
{
int row, col,i;
int **arr ;
printf ("Enter Row and Column\n");
scanf("%d %d",&row,&col );
printf("%d %d\n",row,col );
**arr = (int **) malloc (sizeof (int)*row);
for (i = 0; i < row; i++)
{
arr[i] = (int *) malloc(sizeof(int)*col);
}
return 0;
}
No Tags on this question yet!
12 / 14
No Discussion on this question yet!
No Tags on this question yet!
13 / 14
No Discussion on this question yet!
No Tags on this question yet!
14 / 14
No Discussion on this question yet!
No Tags on this question yet!



