Broadcom Ltd Interview Questions and Answers for 5 years Experience
1 / 12
No Discussion on this question yet!
No Tags on this question yet!
2 / 12
#include
int main()
{
int x;
scanf("%d",&x);
if((x)&&!(x&(x-1)))
{
printf(" %d is power of 2\n",x);
}
else
{
printf(" %d not power of 2 \n",x);
}
}
No Tags on this question yet!
3 / 12
void deleteNodeWithoutHead(struct Node* pos)
{
if (*pos == NULL) // If linked list is empty
return;
else {
struct Node* temp = pos->next;
// Copy data of the next node to current node
pos->data = pos->next->data;
// Perform conventional deletion
pos->next = pos->next->next;
free(temp);
}
return 0;
}
No Tags on this question yet!
4 / 12
Use 2 pointers:-
pNthNode
pTemp
Both the nodes point to the HEAD of the list. pNthNode starts moving only after pTemp has moved n nodes forward. From there, both nodes move forward until pTemp reaches NULL.
pNthNode now points at the nth node from the end.
/*
Defining a function to find the nth node from the end.
*/
struct node * nthNodeFromEnd(struct node * head, int n)
{
// we need to find the nth node from the end.
struct node * pTemp = head;
struct node * pNthNode = head;
int nCurrentElement = 0;
int counter = 0;
while(counter != n)
{
pTemp = pTemp -> next;
counter++;
}
while(pTemp != NULL)
{
pNthNode = pNthNode -> next;
pTemp = pTemp -> next;
}
return pNthNode;
}
No Tags on this question yet!
5 / 12
Things which are all changeable is volatile.
for example, int a=5;
a=a+1; //value changes,this is volatile.
by default all variables are volatile.
No Tags on this question yet!
6 / 12
No Discussion on this question yet!
No Tags on this question yet!
7 / 12
No Discussion on this question yet!
No Tags on this question yet!
8 / 12
No Discussion on this question yet!
No Tags on this question yet!
9 / 12
#define my_sizeof(type) (char *)(&type+1)-(char*)(&type)int main(){ double x; printf("%d", my_sizeof(x)); getchar(); return 0;} |
No Tags on this question yet!
10 / 12
No Discussion on this question yet!
No Tags on this question yet!
11 / 12
No Discussion on this question yet!
No Tags on this question yet!
12 / 12
No Discussion on this question yet!
No Tags on this question yet!
1 / 11
No Discussion on this question yet!
No Tags on this question yet!
2 / 11
No Discussion on this question yet!
No Tags on this question yet!
3 / 11
No Discussion on this question yet!
No Tags on this question yet!
4 / 11
No Discussion on this question yet!
No Tags on this question yet!
5 / 11
No Discussion on this question yet!
No Tags on this question yet!
6 / 11
No Discussion on this question yet!
No Tags on this question yet!
7 / 11
No Discussion on this question yet!
No Tags on this question yet!
8 / 11
No Discussion on this question yet!
No Tags on this question yet!
9 / 11
hello
No Tags on this question yet!
10 / 11
No Discussion on this question yet!
No Tags on this question yet!
11 / 11
No Discussion on this question yet!
No Tags on this question yet!
1 / 8
No Discussion on this question yet!
No Tags on this question yet!
2 / 8
No Discussion on this question yet!
No Tags on this question yet!
3 / 8
No Discussion on this question yet!
No Tags on this question yet!
4 / 8
No Discussion on this question yet!
No Tags on this question yet!
5 / 8
No Discussion on this question yet!
No Tags on this question yet!
6 / 8
No Discussion on this question yet!
No Tags on this question yet!
7 / 8
No Discussion on this question yet!
No Tags on this question yet!
8 / 8
No Discussion on this question yet!
No Tags on this question yet!
1 / 8
No Discussion on this question yet!
No Tags on this question yet!
2 / 8
No Discussion on this question yet!
No Tags on this question yet!
3 / 8
1. pkt flow,
2. L2 learning,
3. port status, and
4. How to check counter at ports
No Discussion on this question yet!
No Tags on this question yet!
4 / 8
No Discussion on this question yet!
No Tags on this question yet!
5 / 8
typedef struct node{
int data;
struct node* next;
}node;
self referential structure
No Tags on this question yet!
6 / 8
No Discussion on this question yet!
No Tags on this question yet!
7 / 8
No Discussion on this question yet!
No Tags on this question yet!
8 / 8
void recLinkedList(struct node *head)
{
struct node *tmp = head->next;
if ( tmp != NULL)
recLinkedList(tmp);
printf("\r\n [%d] \r\n", tmp->data);
}
No Tags on this question yet!
1 / 17
If there is only 1 bag with forgeries, then take 1 coin from the first bag, 2 coins from the second bag . . . 10 coins from the tenth bag and simply weigh the picked coins together !
If there were no forgeries, you know that the total weight should be (1+2+3+ . . . +10) = 55 grams.
But if, for example, the weight is 55.3 grams, then you know that 3 coins are forgeries, so that must be bag 3. So, that solves it.
No Tags on this question yet!
2 / 17
Make a table.
Bag 1 Bag 2 Sum
1 1 2
1 2 3
1 3 4
1 4 5
1 5 6
.
.
.
5 1 6
5 2 7
5 3 8
5 4 9
5 5 10
5 6 11
i) Then count the total number of outcomes.
There are 30 in all (5x6).
Then count the times that the ball from Bag 1 is the same as Bag 2.
There are 5 of those (1-1,2-2,3-3,4-4,5-5).
So the probability of two balls identical is
P=5/30=1/6
ii) Count the number of sums that equal 9.
There are 3 outcomes (3-6,4-5,5-4).
There are 30 total outcomes.
No Tags on this question yet!
3 / 17
No Discussion on this question yet!
No Tags on this question yet!
4 / 17
No Discussion on this question yet!
No Tags on this question yet!
5 / 17
No Discussion on this question yet!
No Tags on this question yet!
6 / 17
No Discussion on this question yet!
No Tags on this question yet!
7 / 17
No Discussion on this question yet!
No Tags on this question yet!
8 / 17
No Discussion on this question yet!
No Tags on this question yet!
9 / 17
No Discussion on this question yet!
No Tags on this question yet!
10 / 17
void mirror(struct Node* node) { if (node==NULL) return; else { struct Node* temp; /* do the subtrees */ mirror(node->left); mirror(node->right); /* swap the pointers in this node */ temp = node->left; node->left = node->right; node->right = temp; }} No Tags on this question yet!
11 / 17
No Discussion on this question yet!
No Tags on this question yet!
12 / 17
Deadlock is a situation where a set of processes are blocked because each process is holding a resource and waiting for another resource acquired by some other process.
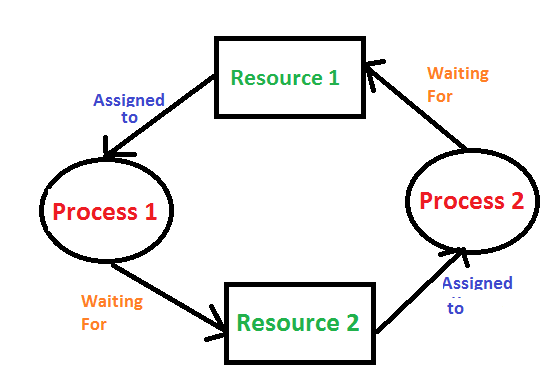
Deadlock can arise if following four conditions hold simultaneously (Necessary Conditions)
Mutual Exclusion: One or more than one resources are non-sharable (Only one process can use at a time)
Hold and Wait: A process is holding at least one resource and waiting for resources.
No Preemption: A resource cannot be taken from a process unless the process releases the resource.
Circular Wait: A set of processes are waiting for each other in circular form.
Methods for handling deadlock
There are three ways to handle deadlock
1) Deadlock prevention or avoidance: The idea is to not let the system into the deadlock state.
2) Deadlock detection and recovery: Let deadlock occur, then do preemption to handle it once occurred.
3) Ignore the problem altogether: If the deadlock is very rare, then let it happen and reboot the system. This is the approach that both Windows and UNIX take.
No Tags on this question yet!
13 / 17
https://techdifferences.com/difference-between-internal-and-external-fragmentation.html
No Tags on this question yet!
14 / 17
No Discussion on this question yet!
No Tags on this question yet!
15 / 17
No Discussion on this question yet!
No Tags on this question yet!
16 / 17
No Discussion on this question yet!
No Tags on this question yet!
17 / 17
brk is used to set the end of the data segment to the value you specify. It says "set the end of my data segment to this address". Of course, the address you specify must be reasonable, the operating system must have enough memory, and you can't make it point to somewhere that would otherwise exceed the process maximum data size. Thus, brk(0) is invalid, since you'd be trying to set the end of the data segment to address 0, which is nonsense.sbrk increments the data segment size by the amount you specify, and returns a pointer to the previous break value. Calling sbrk with 0 is valid; it is a way to get a pointer to the current data segment break address.malloc is not a system call, it's a C library function that manages memory using sbrk. According to the manpage, malloc(0) is valid, but not of much use:If size is 0, then malloc() returns either NULL, or a unique pointer value that can later be successfully passed to free().
brk(0), sbrk(0) and malloc(0) are not equivalent: the first of them is invalid, the second is used to obtain the address of the program's break, and the latter is useless.malloc and brk or sbrk throughout your program. mallocassumes it's got full control of brk and sbrk, if you interchange calls to malloc and brk, very weird things can happen.On success, brk() returns zero, and sbrk() returns a pointer to the start of the new area. On error, -1 is returned, and errno is set to ENOMEM.
No Tags on this question yet!
1 / 8
No Discussion on this question yet!
No Tags on this question yet!
2 / 8
No Discussion on this question yet!
No Tags on this question yet!
3 / 8
No Discussion on this question yet!
No Tags on this question yet!
4 / 8
No Discussion on this question yet!
No Tags on this question yet!
5 / 8
No Discussion on this question yet!
No Tags on this question yet!
6 / 8
No Discussion on this question yet!
No Tags on this question yet!
7 / 8
No Discussion on this question yet!
No Tags on this question yet!
8 / 8
No Discussion on this question yet!
No Tags on this question yet!


