Interview Questions for Cisco cisco interview questions and answers
1 / 8
No Discussion on this question yet!
No Tags on this question yet!
2 / 8
No Discussion on this question yet!
No Tags on this question yet!
3 / 8
No Discussion on this question yet!
No Tags on this question yet!
4 / 8
When memory allocation is done, the actual heap space allocated is one word larger than the requested memory. The extra word is used to store the size of the allocation and is later used by free( )
No Tags on this question yet!
5 / 8
No Discussion on this question yet!
No Tags on this question yet!
6 / 8
No Discussion on this question yet!
No Tags on this question yet!
7 / 8
No Discussion on this question yet!
No Tags on this question yet!
8 / 8
No Discussion on this question yet!
No Tags on this question yet!
1 / 9
No Discussion on this question yet!
No Tags on this question yet!
2 / 9
No Discussion on this question yet!
No Tags on this question yet!
3 / 9
No Discussion on this question yet!
No Tags on this question yet!
4 / 9
If ()
{
printf("I am in if");
}
else
{
printf("I am in Else");
}
change the code something like
If ( ! printf("I am in if") ) <
{
printf("I am in if");
}
else
{
printf("I am in Else");
}
No Tags on this question yet!
5 / 9
Non-Recursive
========
void reverse(struct node ** head)
{
struct node* prev = NULL;
struct node* current = *head;
struct node* next;
while (current != NULL)
{
next = current->next;
current->next = prev;
prev = current;
current = next;
}
*head = prev;
}
This trick might help you
there are three pointer ( prev, current, next)
next = current*
current* = prev
prev = current
current = next
if we see from above logic then before = is like top to bottom then bottom to top .
* marked pointer will have next.
Recursive
=======
struct node * recLinkedList(struct node *head, struct node *prev)
{
struct node *tmp = head->next;
head->next = prev;
if ( tmp != NULL)
recLinkedList(tmp, head);
return head
}
int main()
{
struct node *head = recLinkedList (head, NULL);
}
No Tags on this question yet!
6 / 9
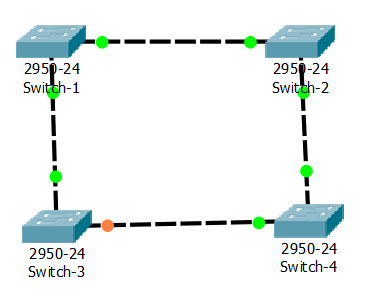
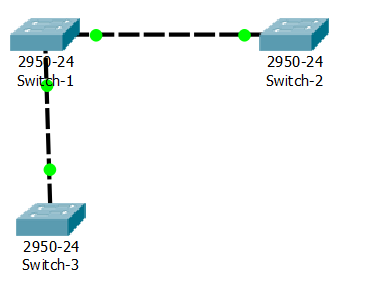
Then he removed switch 4 and ask same to explain.
No Discussion on this question yet!
No Tags on this question yet!
7 / 9
No Discussion on this question yet!
No Tags on this question yet!
8 / 9
No Discussion on this question yet!
No Tags on this question yet!
9 / 9
No Discussion on this question yet!
No Tags on this question yet!
1 / 6
No Discussion on this question yet!
No Tags on this question yet!
2 / 6
No Discussion on this question yet!
No Tags on this question yet!
3 / 6
No Discussion on this question yet!
No Tags on this question yet!
4 / 6
No Discussion on this question yet!
No Tags on this question yet!
5 / 6
ex. 12->3->1->11->23->44-> ------->100
After first iteration
12->11->23->44-> ------->100
after second iteration
12->44-> ------->100
No Discussion on this question yet!
No Tags on this question yet!
6 / 6
No Discussion on this question yet!
No Tags on this question yet!
1 / 6
Host-1 ----------ping------- Host-2
No Discussion on this question yet!
No Tags on this question yet!
2 / 6
No Discussion on this question yet!
No Tags on this question yet!
3 / 6
No Discussion on this question yet!
No Tags on this question yet!
4 / 6
No Discussion on this question yet!
No Tags on this question yet!
5 / 6
A bridge is a product that connects a local area network (LAN) to another local area network that uses the same protocol (for example, Ethernet or Token Ring). You can envision a bridge as being a device that decides whether a message from you to someone else is going to the local area network in your building or to someone on the local area network in the building across the street.
Benefit :
It work at data link layer and it is capable of handling physical addressing, so it reduce the un-necessary traffic.
No Tags on this question yet!
6 / 6
a) When memory block requires to be copied then memcpy is useful
when data in the form of string need to be copied then strncpy is useful because of the natural advantage of '\0' terminated string.
b) memcpy() can copy data with embedded null characters.
strncpy will copy the string to the maximum of either the number of characters given or the position of the first occurrence of null character, i.e '\0' , and reset will be filled with 0
No Tags on this question yet!
1 / 5
No Discussion on this question yet!
No Tags on this question yet!
2 / 5
No Discussion on this question yet!
No Tags on this question yet!
3 / 5
No Discussion on this question yet!
No Tags on this question yet!
4 / 5
No Discussion on this question yet!
No Tags on this question yet!
5 / 5
No Discussion on this question yet!
No Tags on this question yet!
1 / 2
No Discussion on this question yet!
No Tags on this question yet!
2 / 2
No Discussion on this question yet!
No Tags on this question yet!
- >> Cisco Interview Question Set 1
- Cisco Interview Question Set 2
- Cisco Interview Question Set 3
- Cisco Interview Question Set 4
- Cisco Interview Question Set 5
- Cisco Interview Question Set 6
- Cisco Interview Question Set 7
- Cisco Interview Question Set 8
- Cisco Interview Question Set 9
- Cisco Interview Question Set 10
- Cisco Interview Question Set 11
- Cisco Interview Question Set 12
- Cisco Interview Question Set 13


